When DDoS Mitigation Isn’t Enough
Back when my partner and I were leading the hosting company’s operations — him on the technical side, myself on the business side — we started noticing a dangerous pattern:
- 🔴 DDoS attacks were growing.
- 🔴 Arbor, our data center’s anti-DDoS system, couldn’t keep up.
- 🔴 Some attacks still got through — causing 10 to 20 minutes of complete outages.
- 🔴 Even “auto-mitigated” attacks caused blips — up to 30 seconds of packet loss.
- 🔴 Some customer workloads, especially clusters, experienced split-brain issues.
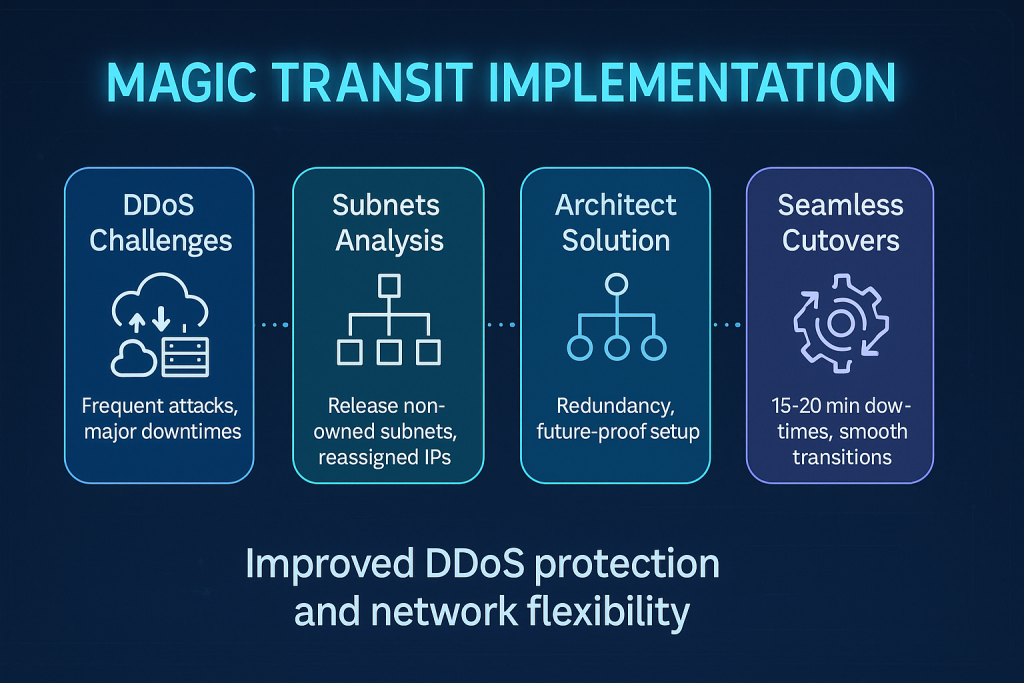
For a hosting platform serving thousands of VMs, these incidents were unacceptable.
We needed to rethink the entire network security strategy — and not just patch it, but rebuild it for the future.
That’s where the idea of a Magic Transit implementation came in.
Why We Chose Magic Transit
We evaluated different vendors, but Cloudflare’s Magic Transit stood out — not just for its world-class DDoS mitigation, but also for what it enabled:
- IP mobility across data centers
- Per-IP routing instead of subnet-level rigidity
- Ability to support customer-owned subnets (BYOIP)
- Improved speed by routing users to the closest Cloudflare edge
- The ability to become data center agnostic
This was more than a protection upgrade — it was an opportunity to future-proof the network.
Step 1: Subnet Ownership, Cleanup, and Planning
To implement Magic Transit, we had to first regain full control over the IP space.
Some subnets were company-owned. Others belonged to the data center. We couldn’t advertise what we didn’t own — so we launched a coordinated internal project:
- Returned all data center-owned subnets
- Reassigned IPs for affected customers
- Helped update DNS, rebuild IP reputation, and adjust systems
- Supported legacy applications and provided guidance
It was detailed, customer-focused work — but critical to making the move.
Step 2: Architecting the Future-Proof Solution
We designed the new network with:
- Redundant BGP connections from Cloudflare to both of our data centers
- Flexible routing that allowed individual IPs to go to any location
- Firewalls configured to handle Cloudflare as the new edge
- The ability to migrate infrastructure between sites without changing IPs
- Tenant-ready design to support BYOIP for client subnets
We weren’t just solving a problem — we were building for scale and independence.
Step 3: Controlled Rollouts and Subnet Cutovers
With the architecture in place, we executed carefully.
- Split subnets into smaller blocks for safer migrations
- Worked with Cloudflare and our data center’s NetOps team to coordinate BGP changes
- Validated everything with a test subnet
- Scheduled multi-team calls for coordinated cutovers
- For critical clients, failovers were pre-triggered to their secondary locations
Each subnet migration averaged 15–20 minutes of downtime, and we ensured no unplanned service interruptions.
Step 4: Deep Troubleshooting, MTU Issues, and Firewall Adjustments
The project wasn’t without challenges:
- We faced MTU problems with customer VPNs
- Encountered unexpected firewall behaviors due to new traffic paths
- Spent hours analyzing packet-level issues to stabilize the new routing flow
But with testing, patience, and collaboration across all teams — we solved each one.
Step 5: Negotiation and Execution at the Business Level
While the technical implementation moved forward, we were also handling:
- Pricing and contract negotiations with Cloudflare
- Ensuring timely termination of Arbor services from our data center
- Coordinating contract timing to avoid double billing
- Aligning internal stakeholders and timelines
This was a full-stack execution — from engineering to finance.
The Outcome of Our Magic Transit Implementation
- ✅ Zero unmitigated DDoS incidents after deployment
- ✅ Faster response to new threats
- ✅ Edge-based acceleration for user traffic
- ✅ Fully mobile IPs across data centers
- ✅ BYOIP support for enterprise customers
- ✅ Huge operational flexibility for future growth
- ✅ Peace of mind for the NetOps team and our clients
It wasn’t just a security upgrade — it was a foundation for next-generation hosting.
Why This Project Mattered to Us
This was one of the most complex and high-impact projects we’ve delivered in our careers.
And it’s also one of the reasons we founded Nubius Solutions.
My partner and I had grown in that company — from hands-on roles to leadership — and delivered high-risk, high-reward projects like this one together.
But we saw something missing in the industry:
A true partner that doesn’t just recommend solutions —
but actually executes them end-to-end with clarity, precision, and care.
That’s why we built Nubius Solutions — to help companies modernize their infrastructure, reduce risk, and scale smarter.
Planning Your Own Magic Transit Implementation?
Whether you’re struggling with DDoS mitigation, legacy IP routing, or preparing to decouple from a data center — we’ve been there.
We don’t just offer advice.
We’ve lived it.
We’ll help you plan, build, execute, and support your infrastructure the right way.
Need expert help for your next infrastructure project?
🔧 See our Custom Projects & Migrations
👉 Talk to us about your network transformation
